Welcome to the latest edition of Pardon The Intrusion, TNW’s bi-weekly newsletter in which we explore the wild world of security. It’s 2020 and Apple is stepping up its privacy game. At the WWDC developers conference held a few weeks ago, Apple highlighted a slew of new security and privacy features that have been added to the upcoming iOS 14 and macOS Big Sur operating systems. There’s a handy list here, but the one feature that caught my attention the most was the introduction of privacy summaries for third-party apps. There’s no denying that most of us don’t bother to read privacy policies and terms of service agreements when signing up for a service. They are long, boring, and mired in obtuse legalese, as if deliberately designed to keep you in the dark. Apple’s proposed solution to deal with this problem is labels — similar to nutritional information on food packaging — that clearly describe how apps use your data. Of course, the idea of a privacy-focused “nutrition label” is not new. But Apple’s approach also has a problem in that it requires app developers to self-report what information they collect and what pieces of data could be used to track you across the web. In other words, for this to work effectively, app developers have to be honest and transparent about what they do with our data. The big question is: will they? That’s not all. What happens when a developer (intentionally) fails to specify all the data that it uses to track its users? Will Apple reject the app from its App Store? Or will it handle this during the review process? And is there a timeline by when all existing apps are expected to come up with their own privacy labels? Back in March, Zoom’s iOS app was caught sending users’ data (such as mobile OS type and version, time zone, device model and carrier, screen size, and disk space) to Facebook even if they didn’t have a Facebook account. What’s more, it chose to not even mention this data sharing agreement in its privacy policy. So it will be interesting to see how Apple actually enforces this requirement. Until then, the idea of a privacy label is just good on paper.
What’s trending in security?
Google pulled over 100 malicious Chrome extensions and 25 Android apps that were found stealing Facebook credentials, an unnamed Chinese bank forced at least two western companies to install malware-infested tax software on their systems, and Microsoft spotted a threat actor distributing malicious Excel documents that requires users to complete a CAPTCHA as a means to escape detection from anti-malware software.
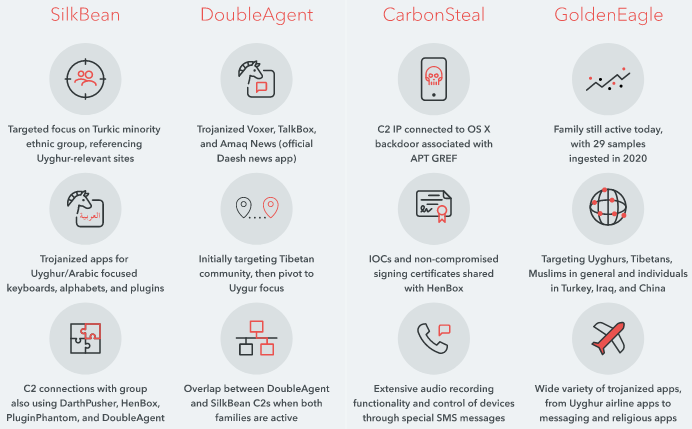
The Federal Communications Commission formally designated Huawei and ZTE as national security threats. But Andy Purdy, Chief Security Officer for Huawei Technologies USA, said these concerns fail to address the broader issue of governments already spying without permission. [FCC / Motherboard] People in Hong Kong are altering their digital footprints or removing their presence entirely from social media following the passage of a new national security law earlier this week. The controversial legislation will outlaw activities of “separatism, subversion, terrorism and foreign interference,” effectively curtailing pro-democracy protests and freedom of speech. [Nikkei Asian Review] After Facebook enlisted an unnamed cybersecurity firm to develop a hacking tool using a flaw in Tails OS to help the FBI track a child predator, the maker of the operating system is still in the dark about the exploit. And yes, there’s no confirmation on whether the FBI used the hacking tool funded by Facebook in other cases. [Motherboard] Hacking collective Anonymous emerged after a long hiatus, returning with a massive trove of data obtained from hundreds of US police departments in an operation dubbed BlueLeaks. The data, which contains a decade’s worth of police training materials and other internal law enforcement data, was published by Distributed Denial of Secrets. [Krebs on Security] Mozilla and Google are set to follow Apple’s footsteps by rejecting HTTPS certificates in their browsers that expire more than 13 months (or 398 days) from their creation date. I wrote about why this matters here. [ZDNet] Researchers have uncovered a surveillance campaign, dating back to at least 2013, which used a slew of Android spyware tools — called SilkBean, DoubleAgent, CarbonSteal, and GoldenEagle — to stalk the Uyghur ethnic minority group, suggesting China’s mobile hacking campaign was broader and more aggressive than previously thought. Newly unearthed evidence has connected the Android malware to a large government defense contractor from the city of Xi’an. [Lookout]
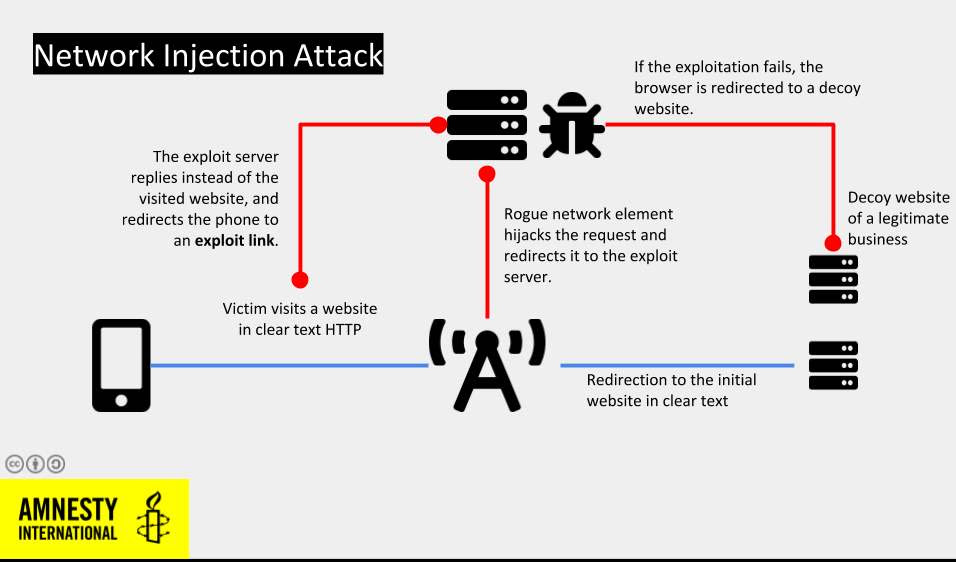
Apple declined to implement 16 new web technologies in its Safari web browser, including Bluetooth, NFC, magnetometer, battery status, proximity sensor, geolocation sensor, and user idle detection APIs, over concerns that they could violate users’ privacy using browser fingerprinting techniques. [ZDNet] Australia announced it’s spending AU$1.35 billion to over the next decade to boost its cybersecurity capabilities in the wake of cyber attacks from a sophisticated “state-based” hacker. [ABC Australia] Thanks to a new iOS 14 feature, TikTok and 58 other apps were caught snooping on your clipboard data. [Ars Technica] Credit card skimming attacks, also known as e-skimming, are becoming more sophisticated. Cybercrime gangs are now hiding the malicious code inside the metadata of a website’s favicon. [The Hacker News] Omar Radi, a prominent activist and journalist from Morocco, had his phone hacked via a network injection attack to install NSO Group’s Pegasus spyware from January 2019 until the end of January 2020. [Amnesty International]
Since the onset of the coronavirus pandemic, there has been a rise in stalkerware, facilitating those with bad intentions to spy on what a partner is up to — by tracking their texts, calls, social media use, and location information. [CyberScoop] US lawmakers are back with a new draft bill, called Lawful Access to Encrypted Data Act, that would end “warrant-proof” encryption, forcing tech companies to build “backdoors” to let law enforcement, with a warrant, access an encrypted device’s contents. But there’s no such thing called a secure backdoor: there’s no way to have a deliberate weakness in encryption without also making it possible for hackers to exploit the flaw. It’s akin to locking your doors and leaving the keys under the doormat. In a separate development, a new bill — Facial Recognition and Biometric Technology Moratorium Act of 2020 — has been introduced with an aim to ban the use of facial recognition technology by federal law enforcement agencies in the US. [Stanford Law / Motherboard] After reports emerged that a Chinese bank forced at least two western companies to install malware-laced tax software called Intelligent Tax on their systems, the threat actor delivered an uninstall tool to remove all traces of the malware. The purpose or actors behind the threat are still unknown. [Trustwave] An analysis of more than one billion leaked credentials has found that one out of every 142 passwords is “123456”. [Ata Hakçıl] The fortnight in data breaches and ransomware attacks: Indiabulls, LG Electronics, University of California, and Twitter.
Data Point
It’s no secret that cybercriminals have mounted a variety of attacksexploiting fears over COVID-19. From sneaky malware to ransomware (called “CryCryptor“) that poses as contact-tracing apps, we’ve seen it all. Now, according to a report from cybersecurity firm Rapid7, malicious coronavirus-related domains are continuing to be registered as new epicenters mushroom across the world. Although the number of daily registrations have fallen from their March peaks, the month of May witnessed over 500 COVID-19 domains, suggested cyberbaddies are still discovering new ways to trick unsuspecting users. Takeaway: “Attackers are unscrupulous when it comes to the lows they will sink to to incite users to fall victim to their lures,” the report said. “Further, the simplicity with which lures can appear and disappear makes actively defending against them impossible.” In general, avoid clicking on links in unsolicited emails and be wary of email attachments. That’s it. See you all in two weeks. Stay safe! Ravie x TNW (ravie[at]thenextweb[dot]com)